Windows 2000
2008/9 Schools Wikipedia Selection. Related subjects: Software
 |
|
| Windows 2000 | |
| (Part of the Microsoft Windows family) | |
| Screenshot | |
 Screenshot of Windows 2000 Professional |
|
| Developer | |
| Microsoft | |
| Web site: www.microsoft.com/windows2000 | |
| Release information | |
| Release date: | December 15, 1999 info |
| Current version: | 5.0 SP4 Rollup 1 v2 (5.0.3700.6690), September 13, 2005 info |
| Source model: | Shared source |
| License: | Microsoft EULA |
| Kernel type: | Hybrid kernel |
| Support status | |
| Extended Support Period until July 13, 2010. Security updates and security-related hotfixes will be provided free of cost. Paid support is still available. | |
Windows 2000 (also referred to as Win2K) is a preemptive, interruptible, graphical and business-oriented operating system designed to work with either uniprocessor or symmetric multi-processor computers. It is part of the Microsoft Windows NT line of operating systems and was released on February 17, 2000. It has been succeeded by Windows XP in October 2001 and Windows Server 2003 in April 2003. It is a hybrid kernel operating system.
Four editions of Windows 2000 were released: Professional, Server, Advanced Server, and Datacenter Server. Additionally, Microsoft sold Windows 2000 Advanced Server Limited Edition and Windows 2000 Datacenter Server Limited Edition, which were released in 2001 and run on 64-bit Intel Itanium microprocessors. While each edition of Windows 2000 was targeted to a different market, they share a core set of features, including many system utilities such as the Microsoft Management Console and standard system administration applications. Support for people with disabilities has been improved over Windows NT 4.0 with a number of new assistive technologies, and Microsoft increased support for different languages and locale information. All versions of the operating system support the Windows NT filesystem, NTFS 3.0, the Encrypting File System, as well as basic and dynamic disk storage. The Windows 2000 Server family has additional features, including the ability to provide Active Directory services (a hierarchical framework of resources), Distributed File System (a file system that supports sharing of files) and fault-redundant storage volumes. Windows 2000 can be installed through either a manual or unattended installation. Unattended installations rely on the use of answer files to fill in installation information, and can be performed through a bootable CD using Microsoft Systems Management Server, by the System Preparation Tool.
Microsoft marketed Windows 2000 as the most secure Windows version ever, but it became the target of a number of high-profile virus attacks such as Code Red and Nimda. More than eight years after its release, it continues to receive patches for security vulnerabilities nearly every month.
History
Windows 2000 is a continuation of the Microsoft Windows NT family of operating systems, replacing Windows NT 4.0. Originally called Windows NT 5.0, then Windows NT 2000, Microsoft changed the name to Windows 2000 on October 27, 1998. It is also the first Windows version that has been released without a code name, though Windows 2000 Service Pack 1 was codenamed "Asteroid" and Windows 2000 64-bit was codenamed "Janus" (not to be confused with Windows 3.1, which had the same codename). The first beta for Windows 2000 was released in September 1997 and several further betas followed until Beta 3 which was released on April 29, 1999. During the development, there was a DEC Alpha build of Windows 2000 but it was abandoned with the second beta. From here, Microsoft issued three release candidates between July and November 1999, and finally released the operating system to partners on December 12, 1999. The public could buy the full version of Windows 2000 on February 17, 2000. Three days before this event, which Microsoft advertised as "a standard in reliability", a leaked memo from Microsoft reported on by Mary Jo Foley revealed that Windows 2000 had "over 63,000 potential known defects". After Foley's article was published, Microsoft blacklisted her for a considerable time: InformationWeek summarized the release "our tests show the successor to NT 4.0 is everything we hoped it would be. Of course, it isn't perfect either." Wired News later described the results of the February launch as "lackluster". Novell criticized Microsoft's Active Directory, the new directory service architecture as less scalable or reliable than its own Novell Directory Services (NDS) alternative.
Windows 2000 was first planned to replace both Windows 98 and Windows NT 4.0. However, that changed later. Instead, an updated version of Windows 98 called Windows 98 Second Edition was released in 1999. Close to the release of Windows 2000 Service Pack 1, Microsoft released Windows 2000 Datacenter Server, targeted at large-scale computing systems with support for 32 processors, on September 29, 2000.
On or shortly before February 12, 2004, "portions of the Microsoft Windows 2000 and Windows NT 4.0 source code were illegally made available on the Internet". The source of the leak remains unannounced. Microsoft issued the following statement:
Microsoft source code is both copyrighted and protected as a trade secret. As such, it is illegal to post it, make it available to others, download it or use it.
Despite the warnings, the archive containing the leaked code spread widely on the file-sharing networks. On February 16, 2004, an exploit "allegedly discovered by an individual studying the leaked source code" for certain versions of Microsoft Internet Explorer was reported.
Architecture
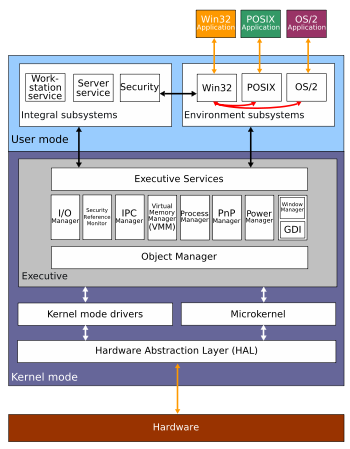
Windows 2000 is a highly modular system that consists of two main layers: a user mode and a kernel mode. The user mode refers to the mode in which user programs are run. Such programs only have access to certain system resources, while the kernel mode has unrestricted access to the system memory and external devices. All user mode applications access system resources through the Executive which runs in kernel mode.
User mode
User mode in Windows 2000 is made of subsystems capable of passing I/O requests to the appropriate kernel mode drivers by using the I/O manager. Two subsystems make up the user mode layer of Windows 2000: the environment subsystem and the integral subsystem.
The environment subsystem is designed to run applications written for many different types of operating systems. These applications, however, run at a lower priority than kernel mode processes. There are three main environment subsystems:
- A Win32 subsystem runs 32-bit Windows applications and also supports Virtual DOS Machines (VDMs) , which allow MS-DOS and 16-bit Windows 3.1x ( Win16) applications to run on Windows.
- An OS/2 environment subsystem supports 16-bit character-based OS/2 applications and emulates OS/2 1.3 and 1.x, but not 32-bit or graphical OS/2 applications as used on OS/2 2.x or later.
- A POSIX environment subsystem supports applications that are strictly written to either the POSIX.1 standard or the related ISO/ IEC standards.
The integral subsystem looks after operating system specific functions on behalf of the environment subsystem. It consists of a security subsystem (which grants/denies access and handles logons) , workstation service (which helps the computer gain network access) and a server service (which lets the computer provide network services).
Kernel mode
Kernel mode in Windows 2000 has full access to the hardware and system resources of the computer. The kernel mode stops user mode services and applications from accessing critical areas of the operating system.
The Executive interfaces with all the user mode subsystems. It deals with I/O, object management, security and process management. It contains various components, including:
- Object manager: an Executive subsystem that all other Executive subsystems must pass through to gain access to Windows 2000 resources. This is essentially a resource management infrastructure service that allows Windows 2000 to be an object oriented operating system.
- I/O Manager: allows devices to communicate with user-mode subsystems by translating user-mode read and write commands and passing them to device drivers.
- Security Reference Monitor (SRM): the primary authority for enforcing the security rules of the security integral subsystem.
- IPC Manager: short for Inter-Process Communication Manager, manages the communication between clients (the environment subsystem) and servers (components of the Executive).
- Virtual Memory Manager: manages virtual memory, allowing Windows 2000 to use the hard disk as a primary storage device (although strictly speaking it is secondary storage).
- Process Manager: handles process and thread creation and termination
- PnP Manager: handles Plug and Play and supports device detection and installation at boot time.
- Power Manager: the power manager coordinates power events and generates power IRPs.
- The display system is handled by a device driver contained in Win32k.sys. The Window Manager component of this driver is responsible for drawing windows and menus while the GDI ( Graphics Device Interface) component is responsible for tasks such as drawing lines and curves, rendering fonts and handling palettes. Windows 2000 introduces alpha blending into the Graphics Device Interface, seen in the fade effect in menus.
The Windows 2000 Hardware Abstraction Layer, or HAL, lies between the physical hardware of the computer and the rest of the operating system. It is designed to hide differences in hardware and therefore provide a consistent platform for applications. It includes hardware specific code that controls I/O interfaces, interrupt controllers and multiple processors.
The hybrid kernel sits between the HAL and the Executive and provides multiprocessor synchronization, thread and interrupt scheduling and dispatching, trap handling and exception dispatching. The hybrid kernel often interfaces with the process manager and is responsible for initializing device drivers at bootup that are necessary to get the operating system up and running.
Common features

Windows 2000 introduced many of the new features of Windows 98 and Windows 98 SE into the NT line, such as the Windows Desktop Update, Internet Explorer 5, Outlook Express, NetMeeting, FAT32 support, Windows Driver Model, Internet Connection Sharing, Windows Media Player, WebDAV support etc. Certain new features are common across all editions of Windows 2000, among them NTFS 3.0, the Microsoft Management Console (MMC), UDF support, the Encrypting File System (EFS), Logical Disk Manager, Image Colour Management 2.0, support for PostScript 3-based printers, OpenType (.OTF) and Type 1 PostScript (.PFB) font support, the Data protection API (DPAPI), an LDAP/ Active Directory-enabled Address Book, usability enhancements and multi-language and locale support. Windows 2000 also comes with several system utilities. Microsoft also introduced a new feature to protect critical system files, called Windows File Protection. This protects critical Windows system files by preventing programs other than Microsoft's operating system update mechanisms such as the Package Installer, Windows Installer and other update components from modifying them.
Microsoft recognized that a serious error or a stop error could cause problems for servers that needed to be constantly running and so provided a system setting that would allow the server to automatically reboot when a stop error occurred. Also included is an option to dump any of the first 64 KB of memory to disk (the smallest amount of memory that is useful for debugging purposes, also known as a minidump), a dump of only the kernel's memory, or a dump of the entire contents of memory to disk, as well as write that this event happened to the Windows 2000 event log. In order to improve performance on servers running Windows 2000, Microsoft gave administrators the choice of optimizing the operating system's memory and processor usage patterns for background services or for applications. Windows 2000 also introduced core system administration and management features as the Windows Installer, Windows Management Instrumentation and Event Tracing for Windows (ETW) into the operating system.
Improvements to Windows Explorer
Windows Explorer has been enhanced in several ways in Windows 2000. It is the first Windows NT release to include Active Desktop, first introduced as a part of Internet Explorer 4.0 (specifically Windows Desktop Update), and only pre-installed in Windows 98 by that time. It allowed users to customize the way folders look and behave by using HTML templates, having the file extension HTT. This feature was abused by computer viruses that employed malicious scripts, Java applets, or ActiveX controls in folder template files as their infection vector. Two such viruses are VBS/Roor-C and VBS.Redlof.a.
The "Web-style" folders view, with the left Explorer pane displaying details for the object currently selected, is turned on by default in Windows 2000. For certain file types, such as pictures and media files, the preview is also displayed in the left pane. Until the dedicated interactive preview pane appeared in Windows Vista, Windows 2000 had been the only Windows release to feature an interactive media player as the previewer for sound and video files. However, such a previewer can be enabled in Windows Me and Windows XP through the use of third-party shell extensions, as the updated Windows Explorer allows for custom thumbnail previewers and tooltip handlers. The default file tooltip displays file title, author, subject and comments; this metadata may be read from a special NTFS stream, if the file is on an NTFS volume, or from an OLE structured storage stream, if the file is a structured storage document. All Microsoft Office documents since Office 95 make use of structured storage, so their metadata is displayable in the Windows 2000 Explorer default tooltip. File shortcuts can also store comments which are displayed as a tooltip when the mouse hovers over the shortcut.
The right pane of Windows 2000 Explorer, which usually just lists files and folders, can also be customized. For example, the contents of the system folders aren't displayed by default, instead showing in the right pane a warning to the user that modifying the contents of the system folders could harm their computer. It's possible to define additional Explorer panes by using DIV elements in folder template files Other Explorer UI elements that can be customized include columns in "Details" view, icon overlays, and search providers: the new DHTML-based search pane is integrated into Windows 2000 Explorer, unlike the separate search dialog found in all previous Explorer versions. This degree of customizability is new to Windows 2000; neither Windows 98 nor the Desktop Update could provide it. The Indexing Service has also been integrated into the operating system and the search pane built into Explorer allows searching files indexed by its database.
NTFS 3.0
Microsoft released the version 3.0 of NTFS (sometimes incorrectly called NTFS 5 in relation to the kernel version number) as part of Windows 2000; this introduced disk quotas, file-system-level encryption, sparse files and reparse points. Sparse files allow for the efficient storage of data sets that are very large yet contain many areas that only have zeros. Reparse points allow the object manager to reset a file namespace lookup and let file system drivers implement changed functionality in a transparent manner. Reparse points are used to implement volume mount points, junctions, Hierarchical Storage Management, Native Structured Storage and Single Instance Storage. Volume mount points and directory junctions allow for a file to be transparently referred from one file or directory location to another.
Encrypting File System
The Encrypting File System (EFS) introduced strong file system-level encryption to Windows. It allows any folder or drive on an NTFS volume to be encrypted transparently by the user. EFS works together with the EFS service, Microsoft's CryptoAPI and the EFS File System Runtime Library (FSRTL). To date, its encryption has not been compromised.
EFS works by encrypting a file with a bulk symmetric key (also known as the File Encryption Key, or FEK), which is used because it takes less time to encrypt and decrypt large amounts of data than if an asymmetric key cipher were used. The symmetric key used to encrypt the file is then encrypted with a public key associated with the user who encrypted the file, and this encrypted data is stored in the header of the encrypted file. To decrypt the file, the file system uses the private key of the user to decrypt the symmetric key stored in the file header. It then uses the symmetric key to decrypt the file. Because this is done at the file system level, it is transparent to the user.
For a user losing access to their key, support for recovery agents that can decrypt files is built in to EFS. A Recovery Agent is a user who is authorized by a public key recovery certificate to decrypt files belonging to other users using a special private key. By default, local administrators are recovery agents however they can be customized using Group Policy.
Basic and dynamic disk storage
Windows 2000 introduced the Logical Disk Manager for dynamic storage. All versions of Windows 2000 support three types of dynamic disk volumes (along with basic disks) : simple volumes, spanned volumes and striped volumes:
- Simple volume, a volume with disk space from one disk.
- Spanned volumes, where up to 32 disks show up as one, increasing it in size but not enhancing performance. When one disk fails, the array is destroyed. Some data may be recoverable. This corresponds to JBOD and not to RAID-1.
- Striped volumes, also known as RAID-0, store all their data across several disks in stripes. This allows better performance because disk reads and writes are balanced across multiple disks.
Accessibility
Microsoft increased the usability of Windows 2000 over Windows NT 4.0 for people with visual and auditory impairments and other disabilities. They included several utilities designed to make the system more accessible, although many of these features were already available with previous versions of Windows:
- FilterKeys: a group of keyboard-related features for people with typing issues, including:
- SlowKeys: Ignore any keystroke not held down for a certain period.
- BounceKeys: Ignore repeated keystrokes pressed in quick succession.
- RepeatKeys: lets users slow down the rate at which keys are repeated via the keyboard's key-repeat feature.
- ToggleKeys: when turned on, Windows will play a sound when the CAPS LOCK, NUM LOCK or SCROLL LOCK key is pressed.
- MouseKeys: lets users move the cursor around the screen via the numeric keypad.
- On-screen keyboard: displays a virtual keyboard on the screen and allows users to press its keys using a mouse or a joystick.
- SerialKeys: lets Windows 2000 support speech augmentation devices.
- StickyKeys: makes modifier keys (ALT, CTRL and SHIFT) become "sticky": a user can press the modifier key, and then release it before pressing the combination key. (Activated by pressing Shift five times quickly.)
- Microsoft Magnifier: A screen magnifier that enlarges a part of the screen the cursor is over.
- Microsoft Narrator: Introduced in Windows 2000, this is a screen reader that utilizes the Speech API.
- High contrast theme: to assist users with visual impairments.
- SoundSentry: designed to help users with auditory impairments, Windows 2000 shows a visual effect when a sound is played through the sound system.
Languages and locales
Windows 2000 introduced the Multilingual User Interface (MUI). Besides English, Windows 2000 incorporates support for Arabic, Armenian, Baltic, Central European, Cyrillic, Georgian, Greek, Hebrew, Indic, Japanese, Korean, Simplified Chinese, Thai, Traditional Chinese, Turkic, Vietnamese and Western European languages. It also has support for many different locales.
Games
Windows 2000 included version 7.0 of the DirectX API, commonly used by game developers on Windows 98. The last version of DirectX that Windows 2000 supports is DirectX 9.0c (Shader Model 3.0), that shipped with Windows XP Service Pack 2. Currently, Microsoft publishes quarterly updates to DirectX 9.0c; these updates contain bug fixes to the core runtime and some additional libraries such as D3DX, XAudio 2, XInput and Managed DirectX components. The majority of games written for recent versions of DirectX can therefore run on Windows 2000, in contrast to Windows NT 4.0, which only provides support for DirectX 3.0.
System utilities
Windows 2000 introduced the Microsoft Management Console (MMC), which is used to create, save, and open administrative tools. Each of these is called a console, and most allow an administrator to administer other Windows 2000 computers from one centralised computer. Each console can contain one or many specific administrative tools, called snap-ins. These can be either standalone (with one function), or an extension (adding functions to an existing snap-in). In order to provide the ability to control what snap-ins can be seen in a console, the MMC allows consoles to be created in author mode or user mode. Author mode allows snap-ins to be added, new windows to be created, all portions of the console tree to be displayed and consoles to be saved. User mode allows consoles to be distributed with restrictions applied. User mode consoles can grant full access to the user for any change, or they can grant limited access, preventing users from adding snapins to the console though they can view multiple windows in a console. Alternatively users can be granted limited access, preventing them from adding to the console and stopping them from viewing multiple windows in a single console.
The main tools that come with Windows 2000 can be found in the Computer Management console (in Administrative Tools in the Control Panel). This contains the Event Viewer — a means of seeing events and the Windows equivalent of a log file, a system information utility, a backup utility, Task Scheduler and management consoles to view open shared folders and shared folder sessions, configure and manage COM+ applications, configure Group Policy , manage all the local users and user groups, and a device manager. It contains Disk Management and Removable Storage snap-ins, a disk defragmenter as well as a performance diagnostic console, which displays graphs of system performance and configures data logs and alerts. It also contains a service configuration console, which allows users to view all installed services and to stop and start them, as well as configure what those services should do when the computer starts.
Windows 2000 comes with two utilities to edit the Windows registry, REGEDIT.EXE and REGEDT32.EXE. REGEDIT has been directly ported from Windows 98, and therefore does not support editing registry permissions. REGEDT32 has the older multiple document interface (MDI) and can edit registry permissions in the same manner that Windows NT's REGEDT32 program could. REGEDIT has a left-side tree view of the Windows registry, lists all loaded hives and represents the three components of a value (its name, type, and data) as separate columns of a table. REGEDT32 has a left-side tree view, but each hive has its own window, so the tree displays only keys and it represents values as a list of strings. REGEDIT supports right-clicking of entries in a tree view to adjust properties and other settings. REGEDT32 requires all actions to be performed from the top menu bar. Windows XP is the first system to integrate these two programs into a single utility, adopting the REGEDIT behaviour with the additional NT features.
The System File Checker (SFC) also comes with Windows 2000. It is a command line utility that scans system files and verifies whether they were signed by Microsoft and works in conjunction with the Windows File Protection mechanism. It can also repopulate and repair all the files in the Dllcache folder.
Recovery Console
The Recovery Console is run from outside the installed copy of Windows to perform maintenance tasks that can neither be run from within it nor feasibly be run from another computer or copy of Windows 2000. It is usually used to recover the system from problems that cause booting to fail, which would render other tools useless.
It has a simple command line interface, used to check and repair the hard drive(s) , repair boot information (including NTLDR) , replace corrupted system files with fresh copies from the CD, or enable/disable services and drivers for the next boot.
The console can be accessed in either of the two ways:
- Booting from the Windows 2000 CD, and choosing to start the Recovery Console from the CD itself instead of continuing with setup. The Recovery Console is accessible as long as the installation CD is available.
- Preinstalling the Recovery Console on the hard disk as a startup option in Boot.ini, via WinNT32.exe, with the /cmdcons switch. In this case, it can only be started as long as NTLDR can boot from the system partition.
Server family features
The Windows 2000 server family consists of Windows 2000 Server, Windows 2000 Advanced Server and Windows 2000 Datacenter Server.
All editions of Windows 2000 Server have the following services and features built in:
- Routing and Remote Access Service (RRAS) support, facilitating dial-up and VPN connections, support for RADIUS authentication, network connection sharing, Network Address Translation, unicast and multicast routing schemes.
- DNS server, including support for Dynamic DNS. Active Directory relies heavily on DNS.
- IPsec support and TCP/IP filtering
- Smart card support
- Microsoft Connection Manager Administration Kit (CMAK) and Connection Point Services
- Support for distributed file systems (DFS)
- Hierarchical Storage Management support including remote storage, a service that runs with NTFS and automatically transfers files that are not used for some time to less expensive storage media
- Fault tolerant volumes, namely Mirrored and RAID-5
- Group Policy (part of Active Directory)
- IntelliMirror, a collection of technologies for fine-grained management of Windows 2000 Professional clients that duplicates users' data, applications, files, and settings in a centralized location on the network. IntelliMirror employs technologies such as Group Policy, Windows Installer, Roaming profiles, Folder Redirection, Offline Files (also known as Client Side Caching or CSC), File Replication Service (FRS), Remote Installation Services (RIS) to address desktop management scenarios such as user data management, user settings management, software installation and maintenance.
- COM+ and MTS
- MSMQ 2.0
- TAPI 3.0
- Security Support Provider Interface (SSPI)
- Integrated Windows Authentication (including Kerberos and SPNEGO authentication).
- MS-CHAP v2 protocol
- Public Key Infrastructure (PKI) and Enterprise Certificate Authority support
- Terminal Services and support for the Remote Desktop Protocol (RDP)
- Internet Information Services (IIS) 5.0
The Server editions include more features and components, including the Microsoft Distributed File System (DFS) , Active Directory support and fault-tolerant storage.
Distributed File System
The Distributed File System (DFS) allows shares in multiple different locations to be logically grouped under one folder, or DFS root. When users try to access a network share off the DFS root, the user is really looking at a DFS link and the DFS server transparently redirects them to the correct file server and share. A DFS root can only exist on a Windows 2000 version that is part of the server family, and only one DFS root can exist on that server.
There can be two ways of implementing a DFS namespace on Windows 2000: either through a standalone DFS root or a domain-based DFS root. Standalone DFS allows for only DFS roots on the local computer, and thus does not use Active Directory. Domain-based DFS roots exist within Active Directory and can have their information distributed to other domain controllers within the domain — this provides fault tolerance to DFS. DFS roots that exist on a domain must be hosted on a domain controller or on a domain member server. The file and root information is replicated via the Microsoft File Replication Service (FRS).
Active Directory
A new way of organizing Windows network domains, or groups of resources, called Active Directory, is introduced with Windows 2000 to replace Windows NT's earlier domain model. Active Directory's hierarchical nature allowed administrators a built-in way to manage user and computer policies and user accounts, and to automatically deploy programs and updates with a greater degree of scalability and centralization than provided in previous Windows versions. It is one of the main reasons many corporations migrated to Windows 2000. User information stored in Active Directory also provided a convenient phone book-like function to end users. Active Directory domains can vary from small installations with a few hundred objects, to large installations with millions. Active Directory can organise and link groups of domains into a contiguous domain name space to form trees. Groups of trees outside of the same namespace can be linked together to form forests.
Active Directory services could only be installed on a Windows 2000 Server, Advanced Server, or Datacenter Server computer, and cannot be installed on a Windows 2000 Professional computer. However, Windows 2000 Professional is the first client operating system able to exploit Active Directory's new features. As part of an organization's migration, Windows NT clients continued to function until all clients were upgraded to Windows 2000 Professional, at which point the Active Directory domain could be switched to native mode and maximum functionality achieved.
Active Directory requires a DNS server that supports SRV resource records, or that an organization's existing DNS infrastructure be upgraded to support this. There must be one or more domain controllers to hold the Active Directory database and provide Active Directory directory services.
Volume fault tolerance
Along with support for simple, spanned and striped volumes, the server family of Windows 2000 also supports fault-tolerant volume types. The types supported are mirrored volumes and RAID-5 volumes:
- Mirrored volumes: the volume contains several disks, and when data is written to one it is also written to the other disks. This means that if one disk fails, the data can be totally recovered from the other disk. Mirrored volumes are also known as RAID-1.
- RAID-5 volumes: a RAID-5 volume consists of multiple disks, and it uses block-level striping with parity data distributed across all member disks. Should a disk fail in the array, the parity blocks from the surviving disks are combined mathematically with the data blocks from the surviving disks to reconstruct the data on the failed drive "on-the-fly".
Deployment
Windows 2000 can be deployed to a site via various methods. It can be installed onto servers via traditional media (such as CD) or via distribution folders that reside on a shared folder. Installations can be attended or unattended. During a manual installation, the administrator must specify configuration options. Unattended installations are scripted via an answer file, or a predefined script in the form of an INI file that has all the options filled in. An answer file can be created manually or using the graphical Setup manager. The Winnt.exe or Winnt32.exe program then uses that answer file to automate the installation. Unattended installations can be performed via a bootable CD, using Microsoft Systems Management Server (SMS) , via the System Preparation Tool (Sysprep), via the Winnt32.exe program using the /syspart switch or via Remote Installation Services (RIS). The ability to slipstream a service pack into the original operating system setup files is also introduced in Windows 2000.
The Sysprep method is started on a standardized reference computer — though the hardware need not be similar — and it copies the required installation files from the reference computer to the target computers. The hard drive does not need to be in the target computer and may be swapped out to it at any time, with the hardware configured later. The Winnt.exe program must also be passed a /unattend switch that points to a valid answer file and a /s file that points to one or more valid installation sources.
Sysprep allows the duplication of a disk image on an existing Windows 2000 Server installation to multiple servers. This means that all applications and system configuration settings will be copied across to the new installations, and thus, the reference and target computers must have the same HALs, ACPI support, and mass storage devices — though Windows 2000 automatically detects Plug and Play devices. The primary reason for using Sysprep is to quickly deploy Windows 2000 to a site that has multiple computers with standard hardware. (If a system had different HALs, mass storage devices or ACPI support, then multiple images would need to be maintained.)
Systems Management Server can be used to upgrade multiple computers to Windows 2000. These must be running Windows NT 3.51, Windows NT 4.0, Windows 98 or Windows 95 OSR2.x along with the SMS client agent that can receive software installation operations. Using SMS allows installations over a wide area and provides centralised control over upgrades to systems.
Remote Installation Services (RIS) are a means to automatically install Windows 2000 Professional (and not Windows 2000 Server) to a local computer over a network from a central server. Images do not have to support specific hardware configurations and the security settings can be configured after the computer reboots as the service generates a new unique security ID (SID) for the machine. This is required so that local accounts are given the right identifier and do not clash with other Windows 2000 Professional computers on a network. RIS requires that client computers are able to boot over the network via either a network interface card that has a Pre-Boot Execution Environment (PXE) boot ROM installed or that the client computer has a network card installed that is supported by the remote boot disk generator. The remote computer must also meet the Net PC specification. The server that RIS runs on must be Windows 2000 Server and it must be able to access a network DNS Service, a DHCP service and the Active Directory services.
Editions
Microsoft released various editions of Windows 2000 for different markets and business needs: Professional, Server, Advanced Server and Datacenter Server. Each was packaged separately.
Windows 2000 Professional was designed as the desktop operating system for businesses and power users. It is the client version of Windows 2000. It offers greater security and stability than many of the previous Windows desktop operating systems. It supports up to two processors, and can address up to 4 GB of RAM. The system requirements are a Pentium processor of 133 MHz or greater, at least 32 MB of RAM, 700 MB of hard drive space, and a CD-ROM drive (recommended: Pentium II, 128 MB of RAM, 2 GB of hard drive space, and CD-ROM drive).
Windows 2000 Server SKUs share the same user interface with Windows 2000 Professional, but contain additional components for the computer to perform server roles and run infrastructure and application software. A significant new component introduced in the server SKUs is Active Directory, which is an enterprise-wide directory service based on LDAP. Additionally, Microsoft integrated Kerberos network authentication, replacing the often-criticised NTLM authentication system used in previous versions. This also provided a purely transitive-trust relationship between Windows 2000 domains in a forest (a collection of one or more Windows 2000 domains that share a common schema, configuration, and global catalog, being linked with two-way transitive trusts). Furthermore, Windows 2000 introduced a Domain Name Server which allows dynamic registration of IP addresses. Windows 2000 Server requires 128 MB of RAM and 1 GB hard disk space, however requirements may be higher depending on installed components.
Windows 2000 Advanced Server is a variant of Windows 2000 Server operating system designed for medium-to-large businesses. It offers clustering infrastructure for high availability and scalability of applications and services, including main memory support of up to 8 gigabytes (GB) on Physical Address Extension (PAE) systems and the ability to do 8-way SMP. It supports TCP/IP load balancing and enhanced two-node server clusters based on the Microsoft Cluster Server (MSCS) in Windows NT Server 4.0 Enterprise Edition. Limited number of copies of an IA-64 version, called Windows 2000 Advanced Server, Limited Edition were made available via OEMs. System requirements are similar to those of Windows 2000 Server , however they may need to be higher to scale to larger infrastructure.
Windows 2000 Datacenter Server is a variant of Windows 2000 Server designed for large businesses that move large quantities of confidential or sensitive data frequently via a central server. Like Advanced Server, it supports clustering, failover and load balancing. Limited number of copies of an IA-64 version, called Windows 2000 Datacenter Server, Limited Edition were made available via OEMs. Its minimum system requirements are normal, but it was designed to be capable of handing advanced, fault-tolerant and scalable hardware—for instance computers with up to 32 CPUs and 64 GBs RAM, with rigorous system testing and qualification, hardware partitioning, coordinated maintenance and change control.
Total cost of ownership
In October 2002, Microsoft commissioned IDC to determine the total cost of ownership (TCO) for enterprise applications on Windows 2000 versus the TCO of the same applications on Linux. IDC's report is based on telephone interviews of IT executives and managers of 104 North American companies in which they determined what they were using for a specific workload for file, print, security and networking services.
IDC determined that the four areas where Windows 2000 had a better TCO than Linux — over a period of five years for an average organization of 100 employees — were file, print, network infrastructure and security infrastructure. They determined, however, that Linux had a better TCO than Windows 2000 for web serving. The report also found that the greatest cost was not in the procurement of software and hardware, but in staffing costs and downtime. While the report applied a 40% productivity factor during IT infrastructure downtime, recognizing that employees are not entirely unproductive, it did not consider the impact of downtime on the profitability of the business. The report stated that Linux servers had less unplanned downtime than Windows 2000 servers. It found that most Linux servers ran less workload per server than Windows 2000 servers and also that none of the businesses interviewed used 4-way SMP Linux computers. The report also did not take into account specific application servers — servers that need low maintenance and are provided by a specific vendor. The report did emphasize that TCO was only one factor in considering whether to use a particular IT platform, and also noted that as management and server software improved and became better packaged the overall picture shown could change.
Current status
Windows 2000 has now been superseded by newer Microsoft operating systems: Windows 2000 Server products by Windows Server 2003, and Windows 2000 Professional by Windows XP Professional.
The Windows 2000 family of operating systems moved from mainstream support to the extended support phase on June 30, 2005. Microsoft says that this marks the progression of Windows 2000 through the Windows lifecycle policy. Under mainstream support, Microsoft freely provides design changes if any, service packs and non-security related updates in addition to security updates, whereas in extended support, service packs are not provided and non-security updates require contacting the support personnel by e-mail or phone. Under the extended support phase, Microsoft continues to provide critical security updates every month for all components of Windows 2000 (including Internet Explorer 5.01 SP4) and paid per-incident support for technical issues. Because of Windows 2000's age, Microsoft is not offering current components such as Internet Explorer 7 for it. They claim that IE 7 relies on security features designed only for Windows XP Service Pack 2 and Windows Vista, and thus porting to the Windows 2000 platform would be non-trivial. Microsoft is strongly advising all users still running Windows 2000 Professional and Server to consider upgrading their operating systems to current operating systems for increased security. While users of Windows 2000 are eligible to receive the upgrade license for Windows Vista or Windows Server 2008, neither of these operating systems can directly perform an upgrade installation from Windows 2000; a clean installation must be performed on computers running Windows 2000.
All Windows 2000 support including security updates and security-related hotfixes will be terminated on July 13, 2010.
Windows 2000 has received four full service packs and one rollup update package following SP4, which is the last service pack. These were: SP1 on August 15, 2000, SP2 on May 16, 2001, SP3 on August 29, 2002 and SP4 on June 26, 2003. Microsoft phased out all development of its Java Virtual Machine (JVM) from Windows 2000 in SP3. Internet Explorer 5.01 has also been upgraded to the corresponding service pack level.
Many Windows 2000 users were hoping for a fifth service pack, but Microsoft cancelled this project early in its development, and instead released Update Rollup 1 for SP4, a collection of all the security-related hotfixes and some other significant issues. The Update Rollup, however, does not include all non-security related hotfixes and is not subjected to the same extensive regression testing as a full service pack. Microsoft states that this update will meet customers' needs better than a whole new service pack, and will still help Windows 2000 customers secure their PCs, reduce support costs, and support existing computer hardware.
Although Windows 2000 is the last NT-based version of Microsoft Windows which does not include Windows Product Activation, Microsoft has introduced Windows Genuine Advantage for certain downloads and non-critical updates from the Download Centre for Windows 2000.
Security criticisms
A number of potential security issues have been noted in Windows 2000. A common complaint is that "by default, Windows 2000 installations contain numerous potential security problems. Many unneeded services are installed and enabled, and there is no active local security policy". In addition to insecure defaults, according to the SANS Institute, the most common flaws discovered are remotely exploitable buffer overflow vulnerabilities. Other criticized flaws include the use of vulnerable encryption techniques.
Computer worms first became publicized when Windows 2000 was the dominant server operating system. Code Red and Code Red II were famous (and much discussed) worms that exploited vulnerabilities of the Windows Indexing Service of Windows 2000's Internet Information Services (IIS). In August 2003, two major worms called Sobig and Blaster began to attack millions of Microsoft Windows computers, resulting in the largest downtime and clean-up cost to that date. The 2005 Zotob worm was blamed for security compromises on Windows 2000 machines at the U.S. Department of Homeland Security, the New York Times Company, ABC and CNN.